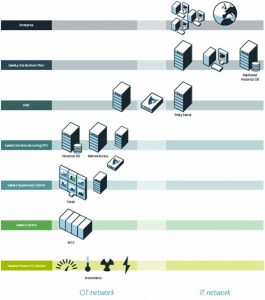
Production facilities being part of the national Critical Infrastructure are endangered by digital threats coming from the Internet. The uninterrupted and correct functioning of ICS is crucial for today’s society. We expect power to come out of sockets, water to flow from taps, ICS systems are key in this process. The ICS production network (OT) is connected to a separate corporate (IT) network environment.
Over the past decade we’ve seen many cases where nation states and/or cybercriminals have successfully attacked and infiltrated production facilities causing huge harm, delay in production and even cost lives. Experience teaches us that the latest methods and complex techniques that are used by top players such as intelligence services quickly find their way to economically-driven cyber criminals. ISC systems and critical infrastructures are strategic targets for Nation States, criminals, terrorists and hacktivist, given the impact that disruptions caused by attacks will have on society.
The network boundary options: Firewall > Air gap > DataDiode. A DataDiode provides great advantages over an (industrial) firewall. By design, a firewall is vulnerable for three reasons: it is firmware, it has software running on it, and the way in which it is configured. Furthermore, the costs of maintaining and managing a firewall are far higher when compared to the Fox DataDiode.
Air gap implies the complete segregation of networks. However, this approach offers a questionable sense of security and has a negative impact on productivity. It is a fact that companies use storage media such as USB sticks. These can be physically exfiltrated and as such provide a means for data leakage. Separating production facilities entirely from any network connection is not an option as important production data needs to be shared with other parts of the organization. When we work together, the sharing of data is both inevitable and valuable. The value of what we do is reflected in the data we share. Data is one of the critical assets in our businesses and it needs to be protected.
The Fox DataDiode is a solution that protects assets from digital threats coming from the internet while at the same time making sure production data can be shared with for example the plants headquarter. Fox DataDiode – The One-Way network connection enforced by the Fox DataDiode offers the highest level of security certification available. It prevents unwanted access to business networks and critical systems, without obstructing free flow of information.
The one-way technology implemented by Fox DataDiode enables organizations to send information from one physical site to another – and not the other way around – giving large organizations the opportunity to centrally monitor their various production sites. This is achieved without opening the individual network and thus keeps its availability and integrity protected. At the same time, information sharing with HQ is still possible. The recommended set-up includes a Fox DataDiodes hardware unit and a proxy server on each side of the unit in order to convert bi-directional protocols into a one-way protocol (on the upstream side) and vice versa (on the downstream side). These proxy servers are equipped with turnkey software solutions to hook into environments and provide secure one-way data transfer from production networks to a corporate environment.
